Which Measure Can Help Control Rfi Effects on Wireless Networks?
Cisco ITE latest or Information technology Essentials v6.0 Terminal Examination Answers All in 1 PC hardware and software (ITE Version 6.00) collection year 2017, 2022 and 2022 Total 100%. IT Essentials has been know as ITE. The following are the questions examination answers. Guarantee Passed. ITE v6.0 Final exam answers All in One has some new update from the old version five. You can review all Final Exam Answers All in Ane. You lot will become passed scored 100% with this version half-dozen.0. Practiced Luck for ITE v6.0 Exam!
Why do laptop computers use CPU throttling techniques?
- to enhance the performance of the CPU
- to reduce the heat that the CPU may generate
- to ensure the CPU is running at its pinnacle speed
- to conserve the battery life by reducing the bus speed between the CPU and RAM
Explanation:CPU throttling is used to conserve ability and increase bombardment life on portable devices. Throttling as well produces less heat.
What is the purpose of RAID adapters?
- to allow older PCI engineering expansion slots to be used
- to provide enhanced audio and graphic capabilities
- to connect multiple storage devices for back-up or speed
- to connect peripheral devices to a PC to improve performance
Explanation:RAID 0 allows "striping" or writing data beyond two difficult drives, simply provides no redundancy. The other RAID versions provide redundancy.
Which type of interface should a customer choose if connecting a unmarried cablevision from a Microsoft Windows computer to output both sound and video to a high definition tv?
- DVI
- HDMI
- PS/2
- DB-15
Explanation:The high definition multimedia interface or HDMI connector is used for outputting both audio and video on a single cablevision. A PS/2 port connects a keyboard or a mouse to a computer. Digital visual interfaces and DB-15 connectors are only used for video output.
What tool is included in the Mac OS X for backing up disks to epitome files and recovering disk images?
- Disk Utility
- Deja Dup
- Deejay Fault-Checking
- Organization Restore
Caption:The Mac Deejay Utility allows an administrator to configure automatic disk backups. The Deja Dup tool is a tool congenital into the Linux OS for backing up data. Deejay Error-Checking is a Windows tool for checking the integrity of files and folders. The Organization Restore tool is a Windows tool for allowing an administrator to curl back the operating arrangement to a previous configuration.
A new technician has joined the Information technology team and is about to service a heavy printer. Which two precautions should be taken to avert any injury when transporting the heavy printer to the service area? (Choose two.)
- Avoid lifting the equipment using the strength in your back.
- Elevator the equipment using the strength in your legs and knees.
- Avoid bending your knees when lifting the printer.
- Bend your dorsum to pick the printer up.
- Avert lifting the printer close to your body.
Explanation:When lifting heavy objects, avoiding bending or using the strength of the back, keeping heavy weights close to the trunk when carrying them, and using the forcefulness of the legs and knee joint to lift something, all contribute to avoid injury.
What type of device provides power to a computer and allows it to be safely shut down in the event of a power loss?
- surge suppressor
- uninterruptible power supply
- standby ability supply
- power inverter
Explanation:An uninterruptible ability supply or UPS contains a battery backup that provides consistent power through brownouts and blackouts until the bombardment power is emptied. Many UPS systems can safely shut down a computer prior to the loss of battery power.
Which mensurate can help control RFI furnishings on wireless networks?
- Ensure the humidity and temperature levels are set equally low as possible.
- Ensure the number of wireless NICs exceeds the number of wireless phones.
- Ensure the wireless network is on a different frequency than the offending source.
- Ensure each wireless NIC is configured to operate at different frequencies from all other wireless NICs.
Explanation:A wireless network (IEEE 802.11) tin be afflicted by radio frequency interference because it shares the same radio frequency range with other devices, such as cordless phones.
What can be tested with a digital multimeter?
- wireless point forcefulness and access bespeak positioning
- basic functionality of estimator ports
- copper cablevision location
- quality of electricity in figurer components
Caption:A digital multimeter tin can exam the integrity of circuits and the quality of electricity in computer components.
When should a technician avert wearing an antistatic wrist strap?
- when installing RAM
- when replacing a ability supply unit
- when installing a hard drive
- when opening a estimator case
Explanation:A power supply unit or CRT monitor are both able to retain big amounts of power later being turned off. These types of devices are likewise dangerous to connect an antistatic wrist strap to. Antistatic wrist straps are commonly worn when upgrading RAM or replacing a difficult bulldoze.
Refer to the exhibit. As part of the procedure of building a calculator, what is the proper order of the commencement three steps in the installation of a power supply?
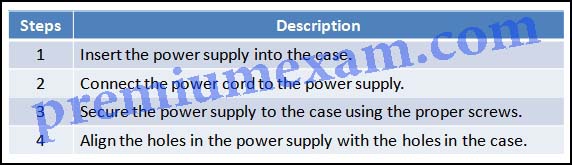
ITE – IT Essentials Final Exam Answers All in One v6.0 2022 2022 100% 01
- Steps 1, 2, 4
- Steps ane, 3, 2
- Steps one, 4, 3
- Steps 2, iii, iv
Explanation:The steps for installing a power supply are as follows:
- Insert the power supply into the instance.
- Align the holes in the power supply with the holes in the case.
- Secure the ability supply to the case with screws.
Power is non practical until all components have been installed.
Which 2 operations can help prevent a mobile device from being tracked without permission? (Choose two.)
- Turn off the GPS when not in employ.
- Use a VPN connectedness whenever possible.
- Set the device to not store credentials.
- Set the device to connect only to known WiFi networks.
- Disable or remove apps that allow connections to the GPS.
Explanation:Device tracking relies on GPS function. Turning off the GPS when not in use and disabling or removing apps that apply the GPS function may prevent a device from being tracked.
What is a feature of a computer ability connector?
- A Molex power connector supplies power to a motherboard.
- A Molex connector and a SATA connector can be used on the aforementioned drive at the aforementioned time.
- A SATA power connector is used to connect to a hd or an optical drive.
- An ATX main power connector supplies ability to a video adapter.
Explanation:Hd drives and optical drives that exercise not accept SATA ability sockets utilize a Molex power connector. A Molex connector and a SATA connector cannot be used on the same drive at the aforementioned time. An ATX chief power connector provides the motherboard with power from the power supply.
Which expansion card can aid in troubleshooting a calculator problem when no video is available?
- BIOS menu
- advanced graphics bill of fare
- USB expansion bill of fare
- POST carte du jour
Explanation:A Mail carte can be installed into a PCI or PCIe slot on the motherboard. When the computer encounters errors on startup, an error code is displayed on the card. Graphics cards and USB expansion cards practice not have this ability. BIOS is found on a chip on the motherboard.
Which two PC settings can exist configured using the BIOS setup utility? (Cull two.)
- POST
- virtualization support
- allocation of memory to applications
- enabling device drivers
- boot sequence
Explanation:The computer boot sequence and support for virtualization can configured from inside BIOS. The calculator operating system typically allocates memory to applications and enables device drivers. POST is typically not configurable.
What cistron should be taken into consideration more than with laptops than with desktops?
- ecology control
- loose cables
- short circuits
- unseated adapter cards
Explanation:Laptops are designed to be mobile and will most likely be used in situations that lack both environmental control and air filtration. Desktop computers are designed to be permanent workstations and are more likely to exist used in controlled environments.
What are three benefits of figurer preventive maintenance? (Cull iii.)
- elimination of the need for repairs
- improvement in information protection
- extension of the life of components
- reduction in the number of equipment failures
- time savings for technicians making repairs
- improvement in RAM access time
Caption:Preventive maintenance can reduce the need for future repairs, simply cannot eliminate them entirely. Preventive maintenance does not impact a technician making repairs. Preventive maintenance has no effect on RAM access time. The remaining options are all benefits of performing preventive maintenance.
Which pace in the troubleshooting procedure is important to aid avoid repeating repair processes that were performed previously?
- identification of the problem
- implementation of the solution
- documentation of the problem and its solution
- preparation of a plan of activeness
A computer user complains of a estimator that freezes up subsequently nigh five minutes of use. The technician checks the computer BIOS to see if there might be a configuration problem that is causing the computer to behave consistently in this manner. While the technician is reviewing the information, the reckoner once more freezes. What is the probable cause of the computer problem?
- The BIOS is corrupt.
- The hard drive is failing.
- The CPU fan is non performance.
- The CMOS bombardment has failed.
Caption:A problem with the CPU or overheating can cause the figurer to freeze.
Why is a full format more than beneficial than a quick format when preparing for a clean OS installation?
- A total format is the only method of installing Windows viii.1 on a PC that has an operating system currently installed.
- A full format volition delete files from the disk while analyzing the disk drive for errors.
- A total format will delete every segmentation on the difficult drive.
- A full format uses the faster FAT32 file system, whereas a quick format uses the slower NTFS file system.
Explanation:A full format removes files from a sectionalization while scanning the disk for bad sectors. A quick format will remove files from a partition just does not scan a disk for bad sectors.
What is the default file system used during a fresh installation of Windows 7?
- NTFS
- HPFS
- FAT16
- FAT32
Explanation:While Windows XP can use either Fat or NTFS, Vista and Windows 7 tin can only be installed on an NTFS partition.
What is the first step an administrator should take when splitting a single partition into multiple partitions?
- Format the partition.
- Assign a drive letter to the segmentation.
- Extend the partition.
- Shrink the partition.
Explanation:The outset step in the process of splitting a partition is to employ the compress volume feature of the Deejay Manager utility. After, the new partition must be formatted and assigned a drive letter.
A user notices that some of the programs that are installed earlier upgrading Windows to a new version no longer function properly after the upgrade. What tin can the user practice to fix this problem?
- Use the System Restore utility.
- Update the driver for the graphics card.
- Run the programs in Compatibility Manner.
- Utilise the recovery partition to reinstall Windows.
Explanation:Compatibility mode allows an application designed for an before version of Windows to operate in later versions. Right-click on the control that starts an application and select Properties to access compatibility mode.
A technician notices that an application is non responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Chore Managing director
- Add together or Remove Programs
- Event Viewer
- Arrangement Restore
Explanation:Use the Task Managing director Performance tab to see a visual representation of CPU and RAM utilization. This is helpful in determining if more than memory is needed. Use the Applications tab to halt an application that is not responding.
A technician has installed a new sound card in a PC but it is not operating correctly. Where should the technician look to investigate driver problems?
- Reckoner Management
- Device Manager
- My Computer
- System Tools
Caption:Device Director can exist used to view information near a item slice of hardware, to view the driver version, to update the driver or gyre it back, or to disable/enable a item device.
After a Windows operating organization has been installed, which program would a technician use to select the programs that will run at startup?
- Ntldr
- Regedit
- Msconfig
- Task Managing director
Explanation:Msconfig is a system utility that tin can exist used to performs diagnostic procedures on the Windows startup files.
Which blazon of network spans a single building or campus and provides services and applications to people within a common organizational structure?
- PAN
- WAN
- LAN
- Human
Caption:A LAN is smaller or more than contained than a WAN, which tin span several cities. A Human is usually contained in one metropolis. A PAN is a very modest network of devices that are located in close proximity to ane another, usually within range of a single person.
A network administrator has finished migrating from a peer-to-peer network to a new client-server network configuration. What are two advantages of the new configuration? (Cull two.)
- The total cost of the new solution is considerably lower.
- Data is more secure in the issue of hardware failures.
- Individual users are in control of their own computers and network resources.
- Data resources and access are centrally controlled.
- Personnel costs are lower because a dedicated network ambassador is no longer necessary.
Explanation:Centralization in a client-server network configuration provides amend monitoring for security, as well as easier access to resources. The full cost may exist higher because a network administrator is required, but reliability and scalability are enhanced.
What are the 4 layers in the TCP/IP reference model?
- application, presentation, net, network access
- application, transport, network, information link
- awarding, transport, internet, network access
- application, presentation, session, transport
- physical, data link, network, transport
Several letters sent to the network administrator are reporting that access to a secure server using HTTPS is declining. After checking recent updates to the visitor firewall, the administrator learns that the firewall is blocking HTTPS. Which port should exist opened to solve the problem?
- 22
- 53
- 80
- 143
- 443
A user wants to map a network drive on a PC that is named "WORK2" and runs Windows 7. The name of the shared resource the user wishes to map to is called "installs" and is located on a workstation called "WORK1". What would exist the correct path for mapping the network drive?
- \\ username\WORK2\\installs
- \\username\countersign/WORK1/installs
- // WORK2/installs
- \\work1\installs
- \\username\Work2\installs
- \WORK2|installs
Explanation:The correct path syntax for mapping a network drive on a PC is \\servername\sharename. Notation that the path statement is not case sensitive. Delight too note that back-slashes ("\") are used in Windows path statements and that 'servername' is the name of the source or location of the resources.
A customer who travels frequently wants to know which technology is the nigh suitable for being connected to the corporate network at all times at low cost. Which network engineering science would a network administrator recommend?
- satellite
- ISDN
- cellular
- microwave
Caption:A customer who travels frequently wants to know which engineering science is the virtually suitable for being connected to the corporate network at all times at low cost. Which network technology would a network ambassador recommend?
What is the difference between cloud computing and a information heart?
- A data center provides access to shared computing resource, wheras a cloud is a individual on-premise facility that stores and processes local data.
- Cloud calculating solutions are network resources and services provided to the clients through the use of services from data centers.
- The data centre makes use of more than devices to process information.
- Data centers require cloud computing but cloud calculating does not require data centers.
Explanation:Cloud service providers use one or more data centers for services and resources such as data storage. A information center is a data storage facility located inside the visitor and maintained by the IT staff or leased from a co-location provider where the maintenance can be done by the provider or the corporate IT staff.
A user complains about being unable to connect to the wireless network. Which two deportment should be role of troubleshooting the wireless connection? (Cull two.)
- Verify that the laptop is plugged into an electrical outlet.
- Reconfigure TCP/IP settings on the laptop.
- Reinsert the laptop battery.
- Try moving the laptop to different places to see if a signal can be detected.
- Verify in the laptop software whether any wireless networks are detected.
Explanation:Also cheque if the computer has a button that enables wireless connectivity.
A technician installed a network adapter in a calculator and wants to examination network connectivity. The ping control tin simply receive a response from local workstations. What could exist causing the trouble?
- The NIC driver is out of appointment.
- The operating system is not uniform with the remote sites.
- The TCP/IP protocol stack is not loaded.
- The default gateway is non set.
Explanation:In order to access remote networks, a host IP configuration must include the address of the device that volition be used to access the Internet or other networks. Pings to remote networks will neglect if the default gateway is incorrect. Considering the user can access local hosts, in that location are no problems with the NIC or operating system.
An Internet service provider help desk-bound technician receives a call from a client who reports that no i at their business tin can reach whatever websites or go their electronic mail. After testing the advice line and finding everything fine, the technician instructs the customer to run nslookup from the command prompt. What does the technician suspect is causing the customer's trouble?
- improper IP address configuration on the host
- hardware failure of the ISR used to connect the customer to the ISP
- bad cables or connections at the client site
- failure of DNS to resolve names to IP addresses
A technician is asked to configure the time that the system must be idle before the difficult disk spins down on all the Windows-based laptops in the company. The technician configured the power options in Windows simply it appears to have no effect. Where should the technician expect to enable ability management?
- Administrative Tools
- BIOS
- Command Prompt
- Safe style
- Arrangement Registry
Explanation:Await for the ACPI power management configuration section in BIOS.
A technician needs to configure a Bluetooth headset for a laptop user. Which 2 steps should the technician take before installing the headset? (Cull 2.)
- Remove the battery.
- Disconnect Air conditioning power.
- Enable Bluetooth in BIOS Setup.
- Ensure that the antistatic wrist strap is attached to a nonpainted portion of the laptop.
- Ensure that the laptop Bluetooth switch is enabled.
Caption:When attaching whatsoever wireless device to a laptop, power does not have to be removed (either Ac or the DC battery). Besides, you do not have to worry about ESD when installing a wireless device.
What laptop component converts DC power to Air conditioning so that the brandish can illuminate?
- inverter
- backlight
- CCFL
- bombardment
- motherboard
Explanation:The backlight (using either CCFL or LED technology) illuminates the back of the display, but the inverter part is what does the conversion of DC to AC for that backlight.
Which airtight-ended question would be appropriate for a technician to use to narrow down the possible problems on a laptop that volition not power on?
- Tin can the laptop operate using the Air-conditioning adapter?
- Have you inverse your password recently?
- What software has been installed recently?
- What were you doing when the problem occurred?
Explanation:Open-ended questions help the technician to place the consequence past allowing the client to elaborate on the outcome.The answers of "What software has been installed recently?" and "What were you doing when the trouble occurred?" are examples of open-ended questions. Closed-ended questions are used to narrow the focus of the problem. Closed-ended questions commonly accept definite answers such every bit aye, no, a date, a time, or other specifics. Both questions of "Have you lot changed your password recently?" and "Can the laptop operate using the AC adapter? are closed-ended questions, just the one relevant to the estimator not powering on is the one containing the inquiry about the Ac adapter.
A technician is troubleshooting the appearance of flashing lines on a laptop screen. What are 2 possible causes of this distortion? (Choose two.)
- Ability to the pixels has been removed.
- The brandish settings have been inverse.
- The GPU is not cooling correctly.
- The LCD cutoff switch is damaged.
- The display is not correctly installed.
Explanation:When flashing lines are appearing on a laptop screen, the most mutual problems are an overheating GPU, faulty GPU, or a brandish that is non connected properly. When the power to the pixels has been cut off, pixels on the screen will announced dead. If the images on a laptop screen are distorted, a technician should verify that the display settings take not been modified.
A user downloads a widget onto his Android phone but is puzzled to encounter that when the widget is touched an app is launched. What is a possible cause?
- The user has downloaded a virus.
- The widget is decadent.
- The security settings of the Android OS have been compromised.
- The widget is associated with the app and this is the normal behavior.
Explanation:Widgets are programs that when installed associate with the application they were built for. This will cause the awarding to launch when the widget icon is touched on the touchscreen of the Android device.
Which component uses the greatest amount of power on nigh mobile devices?
- LCD screen
- camera
- CPU
- media histrion
Explanation:The LCD screen consumes the most power on most mobile devices. The CPU, camera, and media player use power, but less extensively than the LCD screen does.
What is the purpose of using the MIME e-mail protocol on mobile devices?
- to enable pictures and documents to exist included in email messages
- to re-synchronize the email business relationship with other devices
- to remotely lock the email account if the device is stolen
- to encrypt the email messages
Explanation:The MIME email protocol allows pictures and documents to exist included in electronic mail messages.
What is an indication that the battery in a mobile device could become physically hazardous and should be immediately replaced?
- if the bombardment only supports the system for a reduced flow of fourth dimension
- if there are signs of swelling
- if the screen effulgence begins to dim
- if the device feels warm to the touch
Explanation:Because a swelling battery is physically hazardous, it should immediately be replaced with a new one from the manufacturer.
A technician is explaining the differences between inkjet printers and laser printers to a client. Which ii comparisons should the technician brand? (Cull two.)
- Inkjet printers are less expensive as an initial purchase than laser printers.
- A laser printer is significantly slower than an inkjet printer.
- Both laser and inkjet printers produce poor quality images.
- The light amplification by stimulated emission of radiation printer output is dry afterwards press, but an inkjet printer may nonetheless accept wet ink on the paper after printing.
- Inkjet printers use plain paper to make economical prints, but light amplification by stimulated emission of radiation printers crave more expensive thermal paper.
For cleaning a light amplification by stimulated emission of radiation printer, what should be used to pick up excess particles of toner?
- a HEPA-capable vacuum
- a lint-gratuitous material
- isopropyl alcohol
- a damp material
Explanation:The toner used in a laser printer consists of microscopic particles. To effectively pick upwards these particles, it is recommended that a vacuum capable of High Efficiency Particulate Air (HEPA) filtration be used.
What characterizes a DDoS set on?
- Many hosts participate in a coordinated attack.
- Infected computers are called daemons.
- It is like shooting fish in a barrel to identify the source of the attack.
- All hosts must be in the same geographic surface area.
Which two countersign control policies should an arrangement implement to ensure stiff passwords? (Choose two.)
- Passwords should be set to expire every 60 days.
- Passwords should contain no more than eight characters.
- Passwords must contain encrypted characters.
- Passwords should contain messages and numbers.
- Passwords should contain only uppercase letters.
A computer technician has been asked to secure all Windows 7 computers by encrypting all the data on each figurer. Which Windows feature should be used to provide this level of encryption?
- BitLocker
- EFS
- TPM
- Windows Update
Explanation:BitLocker is a Windows characteristic that can be used to encrypt the entire difficult drive volume. Encrypting File System (EFS) is a Windows characteristic that can be used to encrypt files and folders linked to a specific user account. TPM is a specialized fleck on the motherboard that stores data specific to the computer system such every bit encryption keys, digital certificates, and passwords. Windows Update is used to update the operating system, not to encrypt data.
The activity of a previously unknown program triggers an warning past Windows firewall. What three options will the user accept for dealing with this consequence? (Choose three.)
- Proceed blocking
- Unblock
- Ask me later
- Deny all
- Plough off
- Plough on
Explanation:If a programme is blocked by Windows firewall, the user will be presented with three options for dealing with this event: Go on blocking, Unblock, or Ask me afterwards.
A technician suspects that a security effect is causing problems with a computer. What two deportment could be performed to test theories of likely cause when troubleshooting the PC? (Choose 2.)
- Log in as a different user.
- Disconnect the computer from the network.
- Search helpdesk repair logs for more information.
- Discuss solutions with the customer.
- Ask the customer open-ended questions about the trouble.
Caption:Several actions tin can be taken past a technician when security issues are suspected as the possible cause of a trouble with a computer. Logging in as a different user or disconnecting the PC from the network to isolate the cause of the trouble are two possible actions.
A telephone call center technician answers a call from a frequent customer who is known to be impatient and lacks experience with computers. The customer has an effect with an application that the telephone call centre supports. The customer informs the technician that the problem had been reported before but the original technician was rude, did not listen, and did not fix the problem. If the technician is confident that the problem tin be resolved past increasing the amount of memory in the figurer, what should the technician do?
- Tell the client to install ii GB of DDR3 PC3-10600 RAM.
- Explain that the original technician is no good and the supervisor volition exist told.
- Propose that the customer purchase a new reckoner.
- Confirm the issues and give detailed instructions to solve the trouble.
Caption:
When dealing with customers, a technician must show professionalism in all aspects. When explaining the solution to solve the trouble, a technician should provide a uncomplicated step-past-step process of instructions. The technician should speak in apparently terms and avoid the industry jargon.
What expectation is divers in the service level agreement between an organization and service vendor?
- guaranteed service response time
- maximum number of service calls per mean solar day
- chain of custody procedures
- communication etiquette rules
Explanation:The service level agreement, or SLA, is a legal understanding between an organization and a service vendor. The agreement is a bounden contract that spells out service expectations of the service vendor. The SLA typically contains response time guarantees, part availability, and time of service availability.
In which circumstance should a level one technician initiate an escalated work club?
- when a customer appears to be very knowledgeable
- when a client demands talking to a particular technician
- when a problem requires expertise from another technician
- when the technician cannot sympathise the problem as explained past the customer
Explanation:The master responsibility of a level ane technician is to gather data from the customer. The level one technician needs to accurately enter all the information into the work order. When the problems are very simple to resolve, a level one technician can take intendance of these without escalating the work club. Even so, when a trouble requires the expertise of a level ii technician, the level one technician initiates an escalated work club then that a level two technician will be involved to solve the problem.
An application appears frozen and is not responding to a mouse or the keyboard. What Windows Bone tool can be used to stop the application?
- Consequence Viewer
- Job Manager
- Device Manager
- Deejay Direction
Explanation:In Task Manager, the awarding or process that is not responding tin can be identified and closed. Device Manager is used to manage devices and their drivers. Disk Direction is used to manage the partition and file systems of storage devices. Event Viewer is used to review the alerts and notifications sent from the organisation.
Which two issues are likely to crusade BSOD errors? (Choose two.)
- out-of-date browser
- RAM failing
- device driver errors
- lack of antivirus software
- ability supply failure
Explanation:Device driver errors are the most likely cause of BSOD errors. Failing RAM tin can likewise create BSOD errors. Software problems such every bit browsers and antivirus do not produce BSOD errors. A power supply failure would prevent the machine from starting.
A user has installed a new FTP client on a reckoner, but is unsuccessful in connecting to an FTP server. Which two cardinal pieces of information should the user ensure are configured correctly on the FTP client? (Cull two.)
- username
- password
- FTP client IP address
- FTP server IP address
- FTP client port number
- FTP server port number
Caption:Without the correct connection information for the FTP server, file transfer services cannot occur.
A technician wants to allow users to backup and restore all the files on their computers, but does not want the users to be able to brand changes to the organization. How should the technician requite users this functionality?
- Grant the users read permissions on all files.
- Give the users administrator rights on their computers.
- Make the users members of a group called Backup Operators.
- Check the Binder is Set for Archiving box in the properties of each folder.
Explanation:It is better to grant permissions at group level than individual permissions. This way any member of a group would accept the corresponding permissions to carry out the permitted tasks and allows for a tighter command of what the group members can do in a given environment. Information technology also makes information technology easier to administer the environment.
A technician who is working on an employee's laptop finds that a number of files that were encrypted on a network server drive are nowadays on the laptop drive in unencrypted grade. What could crusade this problem?
- Encrypted files cannot be transferred beyond a network.
- The new calculator doesn't have an NTFS partition.
- The network proxy decrypted the information to browse it for malware.
- The sensitive data was transferred with the FTP protocol.
Caption:When encrypted files are transferred to a new computer that is not using an NTFS formatted hard drive, the files will no longer be encrypted.
Lucifer the facility access control devices to the correct descriptions. (Not all options are used.)
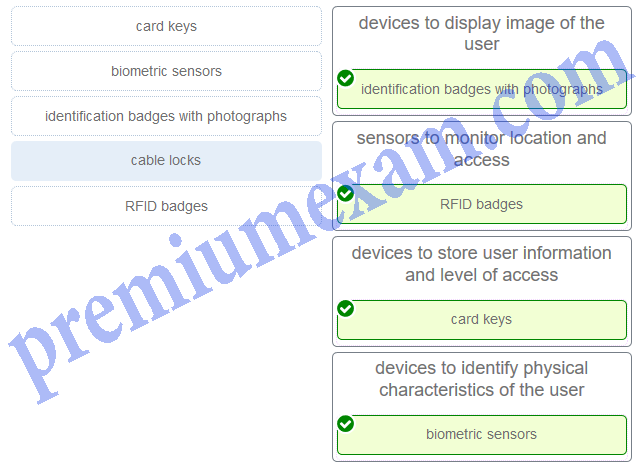
ITE – IT Essentials Final Examination Answers All in One v6.0 2022 2022 100% 02
Which type of input device can identify users based on their voice?
- digitizer
- KVM switch
- biometric identification device
- scanner
Explanation:A biometric identification device is an input device that tin place a user based on a unique physical feature such as a fingerprint or voice. A digitizer is used with a stylus pen to design and create images or blueprints. A scanner is used to digitize an image or document. A KVM switch can connect multiple computers to i keyboard, monitor, and mouse.
What type of external storage should be used by a technician to dorsum up over ii TB of music and video data files?
- CompactFlash card
- external flash drive
- external difficult drive
- Secure Digital card
Caption:An external difficult drive will provide for the largest amount of information storage for bankroll up the music and video data files. CompactFlash and Secure Digital card technology does non support every bit much information storage every bit an external hard drive. A USB flash bulldoze does not hold as much information storage as an external difficult drive.
What is the purpose of a Safety Data Canvass?
- to specify procedures for dealing with potentially hazardous materials
- to specify procedures in designing and building common figurer systems
- to specify procedures for the operation of sensitive components and prevention of electrostatic discharge
- to specify procedures in the employ of humidity control and prevention of wet damage
Explanation:A Safety Data Sheet is a fact sheet that summarizes information near textile identification, including hazardous ingredients that can impact personal health, fire hazards, and first-aid requirements. The SDS explains how to dispose of potentially hazardous materials in the safest style.
Which solution should be used to clean a CPU and a heat sink?
- soap and water
- rubbing alcohol
- a diluted ammonia solution
- isopropyl alcohol
Explanation:Isopropyl booze should be used to clean the surface of a estrus sink and CPU. All the other solutions incorporate impurities which may impairment the CPU.
Which two types of expansion slots would be used by a wireless NIC in a reckoner today? (Cull 2.)
- PCIe
- AGP
- PCI
- DIMM
- ISA
Explanation:Wireless NICs use PCI and PCIe expansion slots on the motherboard. AGP is for a video bill of fare, ISA is an obsolete expansion slot type, and DIMM slots hold RAM modules.
When a PC is being assembled, what component is connected to the motherboard with a SATA cable?
- the optical drive
- the network interface carte du jour
- the video card
- the power supply
Caption:SATA cables, or serial ATA cables, are used to bear data from drives to the motherboard.
A technician is troubleshooting a computer that is experiencing hardware failure detected by the BIOS. What is i fashion this failure is indicated?
- The reckoner automatically boots into Prophylactic Mode and displays a warning on the screen.
- The screen flashes with a red background and displays a warning message.
- The computer emits a pattern of beeps indicating the failing device.
- The computer returns an error message that indicates the I/O accost of the failing device.
Explanation:Beep codes are a result of Post and these vary between computer vendors based on what BIOS is installed.
Which three features tin be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption
- TPM
- file encryption
- TKIP central
- passwords
Explanation:Passwords, drive encryption, and TPM are BIOS configurable security features. File encryption, TKIP cardinal, and MAC filtering are security features not configured within BIOS.
What is the most important reason for a company to ensure that computer preventive maintenance is done?
- Preventive maintenance provides an opportunity for junior technicians to obtain more than feel in a non-threatening or trouble surroundings.
- Preventive maintenance helps to protect the estimator equipment against time to come problems.
- Preventive maintenance allows the Information technology department to regularly monitor the contents of user difficult drives to ensure computer utilise policies are being followed.
- Preventive maintenance enables the IT manager to check on the location and country of the reckoner avails.
Explanation:Preventive maintenance includes tasks such equally cleaning the device, which can prolong the life of the device.
A technician opens upward a PC to work on information technology, and finds that it is very dusty inside. What should the technician do?
- Ignore the grit, as information technology does not affect the figurer.
- Employ a lint-free cloth sprayed with a cleaning solution to remove excess dust.
- Apply a can of compressed air to remove backlog grit.
- Utilise a moistened cotton swab to remove excess dust.
Caption:Grit within a PC tin cause overheating, fan malfunction, and other problems. Liquid should not be used inside a PC to remove dust; compressed air volition blow the dust abroad from where it has accumulated. Always hold the can upright and avoid dripping whatever of the fluid on the PC. Care should be taken to brand sure that the compressed air does non blow materials back within the case, and that fan blades are stabilized while using the compressed air.
Which congenital-in tool is bachelor on a Mac Os X machine to perform disk backups?
- Disk Utility
- Deja Dup
- Finder
- Time Machine
Explanation:Fourth dimension Machine is an automatic backup utility in the Mac OS. The Mac Disk Utility allows an administrator to configure disk backups. The Deja Dup tool is a tool built into the Linux OS for backing upwards data. Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file organisation.
A computer technician performed a number of actions to right a problem. Some actions did non solve the problem, just somewhen a solution was found. What should be documented?
- everything that was washed to try to solve the problem
- only the solution, because this solved the trouble
- only the failed attempts, then that time to come technicians volition know what not to effort
- a clarification of the problem and solution
Caption:Everything that was done to solve a problem should be documented, including failed attempts and the eventual solution. A description of the trouble would accept been previously documented.
After a computer is powered on, Windows 7 fails to starting time. What initial procedure would a technician utilize to deal with this failure?
- Create a Organization Repair Disc and restore the image.
- Press the F12 key during the boot process and start the computer in Safe Mode.
- Boot from a Windows 7 installation media and access the Arrangement Restore utility.
- Access the Control Panel and cull Restore Files from Backup from the System and Security menu.
Caption:There are many reasons that could crusade a PC not to offset, including hardware failure, MBR abuse, a hardware driver that was not installed properly, etc. I approach for PC troubleshooting is to kicking the PC with a Windows 7 installation DVD and use the System Restore utility to restore the organisation. To access Safe Mode, nosotros need to printing theF8central (not the F12 cardinal). The other ii options assume that the PC can first.
What are 2 advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows faster admission to external peripherals such as a USB drive.
- NTFS supports larger files.
- NTFS provides more security features.
- NTFS allows faster formatting of drives.
- NTFS is easier to configure.
- NTFS allows the automatic detection of bad sectors.
Explanation:The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file arrangement-dependent.
What type of hard drive contains flash retention for caching frequently used data but stores the virtually of the data on a magnetic hd drive?
- USB flash drive
- solid-country drive
- embedded multimedia card
- solid-state hybrid deejay
Explanation:The solid-state hybrid deejay is a bulldoze that allows for the storage of information on a magnetic hard disk while utilizing flash retentivity for caching often used information. This is a cheaper culling to using a solid-country drive.
What does %USERPROFILE% represent in the path C:\Users\%USERPROFILE%\AppData\Local\Temp?
- the location of the Documents folder of a particular user
- an environment variable that is gear up by the operating system
- a variable fix by the administrator for each user of the organization
- a fixed value that represents the level of access of a user to system files
Which technology provides a solution for PC virtualization?
- hypervisor
- server clustering
- Terminal Services
- RAID
Caption:Microsoft provides software, Virtual PC, which is a type of hypervisor that creates and manages virtual machines on a host computer.
What are 2 consequences of setting an wrong boot social club in the system BIOS? (Choose two.)
- The computer locks up without whatsoever error letters.
- The reckoner displays a "BOOTMGR is missing" fault after Postal service.
- The computer displays an "Invalid Boot Deejay" fault after POST.
- The computer continually restarts without displaying the desktop.
- The figurer displays an 'Inaccessible Boot Device' error after Mail service.
Explanation:When the boot social club is not set correctly in the BIOS, the BIOS may non exist able to locate a valid Os to boot the computer because the BIOS is non configured to look at the correct drive. Error messages, such as "BOOTMGR is missing", "Invalid Boot Deejay", or "Missing NTLDR" may display.
Which layer of the OSI model is responsible for physical addressing and the procedures used to access media?
- application
- data link
- network
- send
Explanation:The data link layer is responsible for concrete addressing and access to the network media. The application layer is responsible for network services to support applications. The network layer of the OSI model is responsible for routing and logical addressing. The send layer is responsible for reliable transport and flow control of data beyond the network.
The electric current IP configuration of a medium size company with several subnets is done manually and is time-consuming. Because of increased network growth, a technician needs a simpler way for IP configuration of workstations. Which service or protocol would simplify the workstation IP configuration task?
- APIPA
- DHCP
- DNS
- ICMP
Which 2 commands could exist used to cheque if DNS name resolution is working properly on a Windows PC? (Choose ii.)
- nslookup cisco.com
- net cisco.com
- ping cisco.com
- nbtstat cisco.com
- ipconfig /flushdns
Explanation:Theping command tests the connection betwixt ii hosts. Whenping uses a host domain name to test the connexion, the resolver on the PC will first perform the name resolution to query the DNS server for the IP address of the host. If the ping command is unable to resolve the domain proper noun to an IP address, an error volition outcome.
Nslookup is a tool for testing and troubleshooting DNS servers.
Which wireless security mode supports government grade security and offers both personal and enterprise authentication?
- WEP
- WPA2
- WPA
- LEAP
Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
- PaaS
- IaaS
- SaaS
- ITaaS
Explanation:Platform equally a service (PaaS) provides a collaborative environment where multiple developers can create software and host an application through a Cloud provider.
A network administrator occasionally asks a technician to brand sure that grit does not accumulate on devices in the network equipment closets. What is the purpose of having the technician practise this job?
- Grit tin can cause network equipment to overheat and cause problems on the network.
- Dust increases electromagnetic interference in nearby connected cables.
- Dust tin encourage insects and other pests to live in the equipment closets.
- Dust is considered a fire run a risk that poses danger to personnel and equipment.
- Dust diminishes the range of wireless services.
Explanation:Dust can clog the cooling vents of network devices. Network equipment is sensitive to heat and may not operate properly or could be damaged by heat build-up.
A technician installed a network adapter in a computer and wants to test network connectivity. The ping command can receive responses from workstations on the aforementioned subnet but not from remote workstations. What could be causing the problem?
- The NIC commuter is out of date.
- The operating system is not compatible with the remote sites.
- The TCP/IP protocol stack is not loaded.
- The default gateway is incorrect.
Caption:The default gateway is the interface IP address of the router that is connected to the local network. The office of the router is to enable communication amongst different networks. If the default gateway is non set or is incorrect, packets that are destined to other networks will not be able to attain the router, and hence there will be no communication to hosts that are located in other networks.
What are three common input devices found on laptops? (Choose three.)
- touchpad
- fingerprint reader
- web camera
- external monitor
- PS/2 keyboard
- Ac power connector
Explanation:Touchpads, fingerprint readers, and web cameras are common devices on modern laptops. An external monitor is an output device. While a PS/2 keyboard is an input device, it is not usually used with laptops. An Air conditioning ability connector provides a method to recharge the battery, but provides no data input to the laptop.?
A user calls the assist desk-bound to report that a mobile device exhibits very slow performance. What could crusade this problem?
- The touchscreen is not calibrated.
- An app is not compatible with the device.
- The operating system is corrupt.
- A power-intensive app is running in the background.
Explanation:A ability-intensive app that is running in the background could consume virtually of the CPU cycles and thus the device would exhibit very slow performance for other apps. If an app is not uniform with the device, the device operating system would freeze. If the operating organisation has encountered an error, the device will fail to reply.
A figurer technician has decided that a problem with a laptop can exist solved past repairing a hardware component. What should be done commencement earlier attempting to repair a hardware component on a laptop?
- Consult the service manual for the laptop.
- Enquire a boyfriend technician for advice.
- Fill-in the BIOS settings.
- Remove the keyboard.
Explanation:Ever consult the service manual before attempting whatsoever repairs. You may consult with another technician for communication, but the transmission should be consulted showtime. Backing up the BIOS settings is not necessary. Removal of the keyboard would occur merely when necessary during repair.
Refer to the showroom. What is true of this mobile device screen?
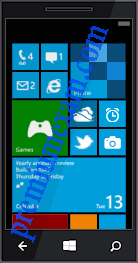
ITE – IT Essentials Final Exam Answers All in One v6.0 2022 2022 100% 03
- Tapping and holding the arrow at the bottom left will display the Home screen.
- Text messages, news, photos and other content can be displayed in the different tiles.
- Icons and buttons are used to represent the different apps on the phone.
- Unpinning an app from this view will uninstall the app from the phone.
- Tile sizes depend on the size of the app.
Explanation:The Windows Phone interface uses tiles to represent apps. Tiles are rectangular areas of a screen that identify the app and may also incorporate active content such equally text messages, news feeds, and photos.
What are two potential risks that could result from rooting or jailbreaking a mobile device? (Choose two.)
- enabling app access to the root directory
- not properly creating or maintaining sandboxing features
- allowing the user interface to exist extensively customized
- improving device performance
- enabling features that are disabled by a cellular carrier
Explanation:
Rooting and jailbreaking mobile devices allows customization of the OS which enables user and app access to the root directory. In addition, rooting and jailbreaking may crusade a device to not properly create or maintain sandboxing features. Both of these tin create security risks to the device. The iii wrong options are all considered potential benefits of rooting and jailbreaking mobile devices
What two tasks should be done regularly to preserve the security and integrity of data and applications on mobile devices. (Choose 2.)
- Execute a factory reset once a month to remove all unidentified malicious software.
- Back up user data on a regular basis.
- Password protect iTunes or Google Play accounts.
- Apply airplane mode if you are accessing the Net at an open up Wi-Fi site.
- Ensure that the operating system software and applications incorporate the latest updates.
- Unmount all unused disk partitions.
Explanation:To help secure and protect the software and data on mobile devices, it is a best practise to do frequent backups. Another best practice is to ensure that all patches and updates are applied to software and applications. Patches and updates usually prepare vulnerabilities besides as introduce new features.
A tire store needs to use carbon re-create paper to print customer invoices so that both the store and the customer have a copy. What is the all-time printer solution?
- piezoelectric printer
- inkjet printer
- thermal printer
- impact printer
Caption:The nigh common blazon of impact printer is a dot matrix printer. Dot matrix printers can use continuous feed or carbon-copy paper.
A user on a dwelling network wants to share a printer from a Windows 7 computer. What must the user do in order for other Windows 7 computers in the house to obtain the proper driver?
- The user must scan the Internet, then download and install the proper driver.
- The person doing the sharing must use the Boosted Drivers button in order to designate how many device drivers are allowed to be downloaded.
- Nix. Windows automatically provides the driver.
- The person doing the sharing must employ the Additional Drivers push in order to designate the driver to be used past the other Windows vii computers.
Explanation:Windows automatically downloads the driver to users who are accessing the shared printer and have the same version of Windows. The Boosted Drivers push button tin can be used to select other operating systems.
Which 3 components are typically institute in laser printer maintenance kits? (Choose three.)
- fuser associates
- primary corona
- pickup rollers
- transfer rollers
- secondary corona
- newspaper trays
Explanation:
Laser printer maintenance kits typically comprise components that wearable and can exist installed with minimal disassembly of the printer. Corona wires are internal components that would require a trained technician to replace. Newspaper trays are components that are not typically replaced during maintenance, merely would be replaced any time if damaged.
What guideline should be followed when establishing a password security policy?
- Passwords should be physically stored in a convenient location.
- Passwords should contain mainly numbers for amend encryption.
- The system administrator should assign passwords to the users.
- Lockout policies should be avoided in order to increase user access.
- An expiration period should exist established so that passwords oft change.
What are three features provided by the TPM module? (Choose three.)
- hashed encryption of the hard drive volume
- security for user authentication information
- back up for Windows backup
- application license protection
- storage of digital certificates
- support for Windows Firewall
Explanation:
The TPM module stores information specific to a host system, such as encryption keys, digital certificates, and passwords. Applications that use encryption tin make use of the TPM fleck to secure things like user authentication information, software license protection, also every bit encrypted files, folders, and disks.
What is the side by side troubleshooting footstep afterwards a theory of probable cause has been established?
- Examination the theory to determine crusade.
- Identify the verbal problem.
- Establish a plan of action.
- Document findings and outcomes.
Explanation:There are six steps in the troubleshooting process.
1. Place the trouble.
2. Establish a theory of likely crusade.
3. Test the theory to determine cause.
4. Establish a plan of action to resolve the problem.
five. Verify total system functionality.
six. Document findings.
Once a technician understands a client complaint, it is mutual to enquire airtight-concluded questions. Which question is a shut-concluded one?
- What happened before the error occurred?
- Is this the first fourth dimension the mistake occurred?
- What happened after the mistake occurred?
- What error messages were displayed when the fault occurred?
Explanation:During the troubleshooting, when the technician listens and understands the computer issues from the customer, some more questions may need to be asked to assemble farther information. These follow up questions should exist targeted and closed-ended questions based on the information that have been provided by the client. The closed-ended questions should be focused on specific aspects and the customer should be able to answer such questions with a uncomplicated "yes" or "no" or with a factual response.
What is a feature of the open up source license of an awarding software?
- It requires registration instead of purchasing.
- Information technology cannot be used for campus-wide deployment.
- It allows users to modify and share the source lawmaking.
- It does non require buy in club to use the software.
- It requires best-selling completion of a professional training class prior to utilise.
Explanation:An open source license is a copyright license for software that allows developers to modify and share the source code that runs the software. Open up source software could be free to use or require purchase. In either example, users accept access to the source code. Open source software could be used as personal software or deployed enterprise wide. User registration is an encouraged optional feature.
Chad, a level one call center technician, receives a client phone call. The customer has an event that Republic of chad does not have the noesis to respond. The client is irritated that Republic of chad cannot provide immediate aid. Which two things should Chad exercise next? (Choose two.)
- Document the reason the client chosen and create a support ticket.
- Inform the customer of the need to call dorsum later.
- Escalate the client to a level two technician.
- Ask the customer further questions to diagnose and attempt to set up the problem.
- Place the customer on concur until the client has time to cool downward.
Explanation:When a customer contacts a call center, the level one technician should always create a ticket and document the problem that the customer is experiencing. If the level one technician is unable to provide assist, the technician should escalate the ticket to a level two technician.
Users in an office complain that the network printer is press vertical lines and streaks on all pages. What is a likely cause of this problem?
- The printer does not accept enough memory.
- The printer has an wrong IP address.
- The wrong print driver is installed.
- The printer drum is damaged.
Explanation:If the printer drum is damaged, pages may have vertical lines or streaks.
A technician is troubleshooting a Windows 7 reckoner that displays an "Invalid Boot Disk" fault bulletin. What would exist the almost likely action the technician should perform to right the upshot?
- Utilize the System Recovery Options to select the correct active segmentation.
- Browse for and remove any virus found.
- Run chkdsk /F /R to ready the hard drive file entries.
- Replace the difficult drive on the computer.
Caption:Typical causes of a computer operating organisation non being found are as follows:
- The partition is not ready every bit active.
- The computer is missing startup files necessary for Windows.
When a user tries to run a program, a missing or corrupt DLL message is displayed. What are ii possible solutions to this problem? (Choose two.)
- Reinstall the right drivers.
- Use the msconfig command to adjust the startup settings for the program.
- Run Windows Startup Repair.
- Run sfc/scannow in Safe Manner.
- Reinstall the program that is associated with the corrupt DLL file.
Explanation:Two possible solutions to a reported missing or corrupt DLL are to reinstall the plan that is associated with the corrupt DLL file or restart the calculator in Condom Manner and run sfc/scannow. Windows Startup Repair is used to solve Windows startup problems. Adjusting the program startup settings by usingmsconfig is applicable only to programs that get-go correctly. Drivers relate to hardware, not to programs.
Which 2 actions can be taken when configuring Windows Firewall? (Choose ii.)
- Enable MAC accost authentication.
- Turn on port screening.
- Manually open ports that are required for specific applications.
- Let a different software firewall to control access.
- Perform a rollback.
Explanation:When a unlike software firewall is installed, Windows Firewall must be disabled through the Windows Firewall command console. When Windows Firewall is enabled, specific ports tin be enabled that are needed by specific applications.
Source: https://examans.com/ite/ite-v6-0/ite-final-exam-answer-v6-0/